Busting a Counterfeit Network Operating Through Meesho
How a Leading Pharma Brand Used Pirates Alert to Unmask a Hidden Seller Ring
Client File
Challenge
While monitoring Meesho via CounterFix, the client flagged multiple suspicious listings of a leading skincare product. A test buy confirmed the items were counterfeit. Though the sellers appeared unrelated, consistent patterns in product presentation and behavior exposed a coordinated network using fake identities.
Objective
Uncover the real seller network behind the counterfeit listings, verify identities, and provide the brand with actionable intelligence for legal and offline enforcement.
Outcomes
- ✓Sellers appeared unrelated at first glance but mimicked the brand’s top skincare product
- ✓Packaging, visuals, and product descriptions indicated coordinated behavior
- ✓Client lacked real identities or legal data to act against the sellers
- ✓Traditional takedown paths were ineffective due to false identities and distributed seller setup
The Solution Strategy
Discover
Define
Design
Develop
Deploy
The Investigation
Pattern Detection Across Sellers
Using CounterFix, multiple Meesho listings were flagged for listing products that closely resembled the client’s top skincare SKU.
Key findings:
- Product visuals and descriptions mirrored the client’s original packaging
- Multiple listings showed similar design patterns and seller behavior, indicating possible coordination
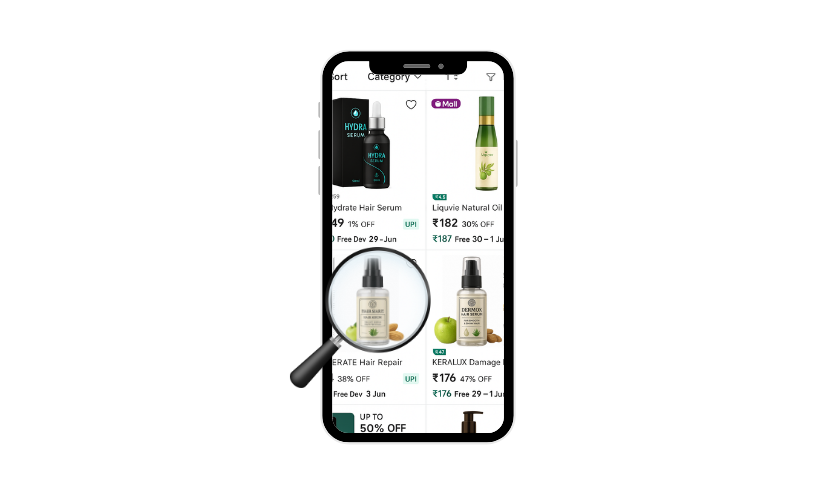
Test Purchase Validation
A controlled purchase was made to verify product authenticity and gather physical evidence.
Key findings:
- Product received was counterfeit and closely mimicked the client’s packaging
- Purchase details linked back to seller accounts and provided invoice documentation

Seller Network Mapping
We used CounterReveal to analyze digital behavior and seller metadata.
Key findings:
- All accounts were operated under one network using proxy seller profiles
- Friends and family members were used as account holders
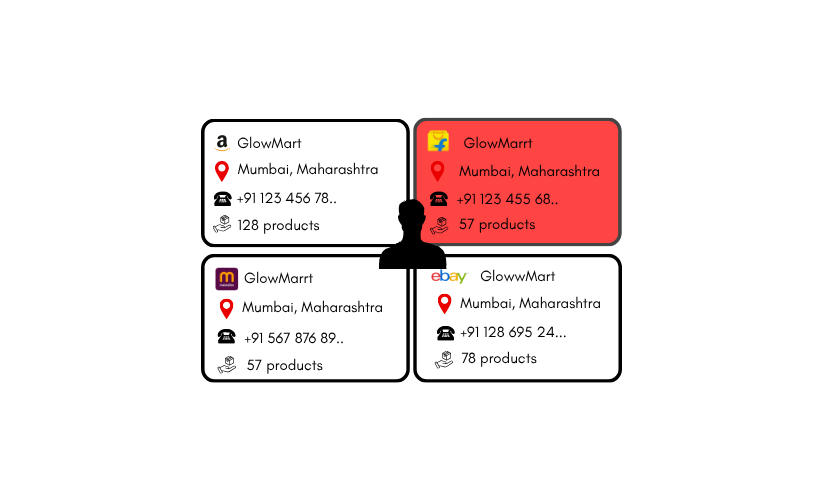
Identity and Financial Linkage
We combined financial analysis with digital tracing to uncover the person behind the network.
Key findings:
- Multiple seller accounts funneled payments to a single bank account
- Real phone numbers and a visual photo of the suspect confirmed centralized control
Enforcement-Ready Report Compilation
All findings were consolidated into a structured, legally admissible report.
Key findings:
- Report included digital links, financial records, and visual proof
- Client’s legal and field teams were equipped to take immediate action
Case Closed: The Results
Key Achievements
- Central operator behind counterfeit listings identified, with evidence linking multiple seller accounts and financial trails
- Multiple fake seller accounts exposed across the platform, revealing a coordinated network using proxy identities
- Verified identities and contact details obtained, including personal, banking, and behavioral data
- Actionable evidence prepared for legal escalation, enabling the client to act swiftly and confidently
- Offline takedown operations initiated with confidence, supported by platform-verified intelligence and a structured enforcement roadmap
"Pirates Alert helped us connect the dots from scattered fake listings to a full-blown counterfeit network. Their tools uncovered not just the sellers but the person pulling the strings. That intelligence was a game-changer for our enforcement efforts. Their support gave us the clarity and confidence to act swiftly and effectively."
Head of Compliance & Brand Protection
Leading Pharma Brand
Facing a similar issue?
Pirates Alert can help you detect, trace, and dismantle hidden networks before the damage spreads.
Start your investigationCase Files
Explore how we've helped brands across industries protect their intellectual property and eliminate threats.